Are Bots exploiting Coronavirus fears?
2020-04-30
Coronavirus is a pandemic that the world has not witnessed in quite some time. International borders are closed. Major sports leagues have suspended their games. Employers have asked their workers to work from home. Normal life has been upended and will remain so for the foreseeable future, as the world struggles to get ahead of the deadly COVID-19 virus.
As the information on the novel virus deluges WhatsApp inboxes and social media feeds, the WHO recently warned of a different type of outbreak in regard to coronavirus: the overabundance of information makes it difficult for people to differentiate between legitimate news and misleading information–which could be disastrous. EU security services have also warned that Russia is aggressively exploiting the coronavirus pandemic to push disinformation and weaken Western society using its bot army.
An Infodemic
Regular monitoring of internet traffic is being processed by bot managers to track the “infodemic” that WHO and the EU security services have warned of. Data shows that bots have upped their game. Organizations from social media, e-commerce, and digital publishing industries have witnessed an unexpected surge in bad bot traffic after the rise of the coronavirus pandemic. These bots were involved in executing various insidious activities, including spreading disinformation, spam commenting, etc.
IT was also found that 58.1% of bots in February could mimic human behavior. This means they can disguise their identity and can create fake accounts on social media sites to post their masters’ propaganda as a genuine user. With such advanced bots, spreading disinformation becomes easy for countries such as Russia.
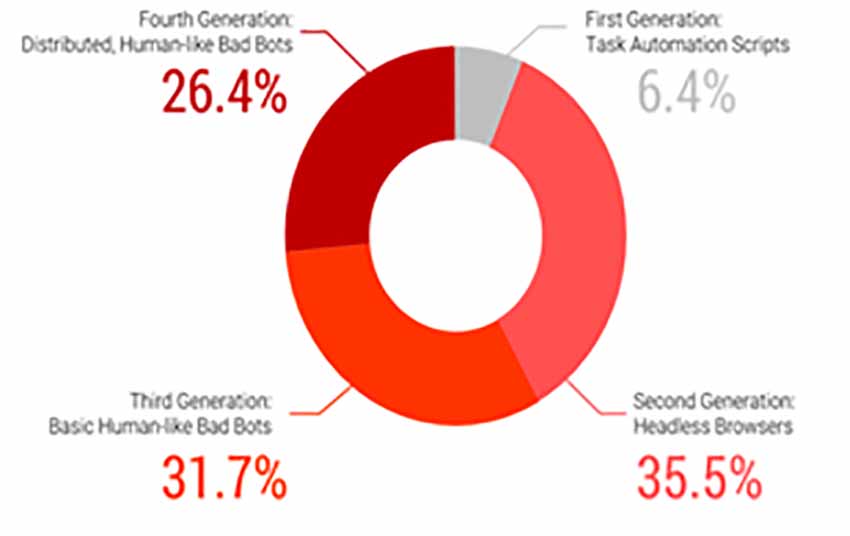
Figure 1: Types of bad bots across industries.
Gaining from the pandemic is not limited to Russia and social media. Given the attention that the “coronavirus” keyword is receiving, cybercriminals and scammers are more vigilant than ever to profit. For example, our research shows there has been an exponential rise in automated attacks on e-commerce and media industry as well. Let’s take a detailed look at it.
Coronavirus Related Articles being scraped by Cybercriminals
Malicious actors are always in search of opportunities to scam people. So much so, they won’t let go of any significant event, whether it’s a natural calamity, a pandemic, or a celebration.
Coronavirus is, in this respect, no different than other events. Fear and a continuous need for latest news provide an excellent breeding ground for automated attacks. A lot of phishing campaigns on the internet today are aimed at luring people with the promise of essential or breaking news on COVID-19, enticing them to click on malicious links or open infected attachments.
In the UK alone, coronavirus scams costed victims over £800k Pound sterling (the equivalent of nearly USD 1M) in one month (February 2020).
Research also suggests that cybercriminals are targeting media and digital publishing sites to scrape their unique content, publish scraped content on malware-ridden shady websites, and scam visitors. 27.7% of traffic on media sites was bad bot involved in automated activity, including scraping in February.
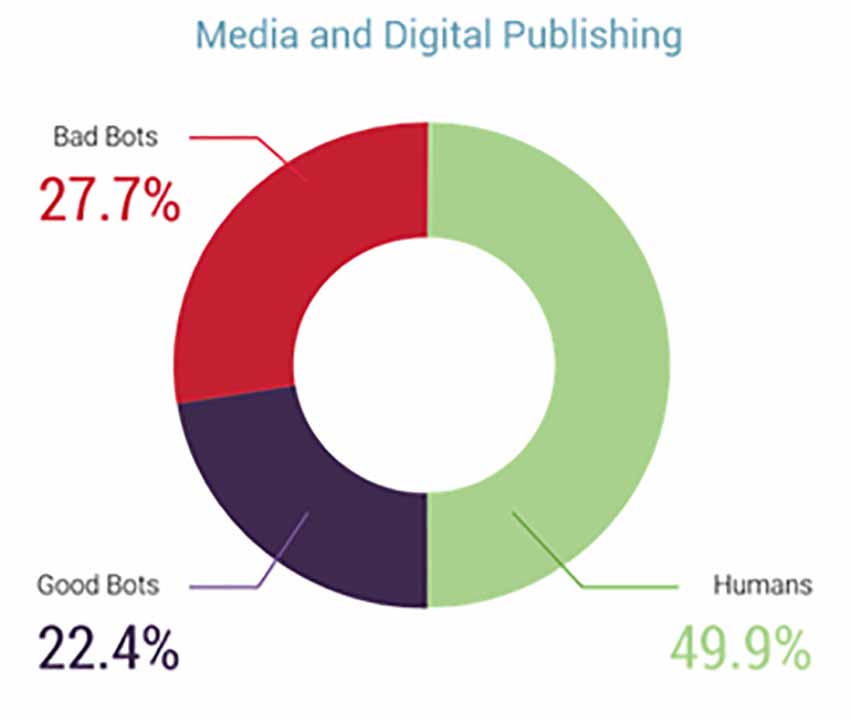
Figure 2: Traffic Distribution of Media and Digital Publishing Sites
Take a look at how cybercriminals are exploiting coronavirus fear and using media sites as facilitators to perform phishing attacks through the following case study. This is a renowned media site that has a dedicated section for coronavirus related news. The figure highlights how bots’ presence gradually increased on the coronavirus section of this website in February and March.
Figure 3: Scraping Attack on the Coronavirus Section of a Renowned Publisher
Bots on this website are attempting scraping. As figure 4 highlights, as soon as an article on coronavirus is published (blue dots), bots are trying to scrape it (red bots). These bots then post the scraped articles on malware-ridden shady websites owned by their masters to lure visitors for scams.
Figure 4: Scraping attack analysis.
Search for Sanitizers and Face Masks by Bots
Bots’ quest to gain from the coronavirus pandemic doesn’t end with media sites; they are also targeting e-commerce websites. With 31.3% of traffic comprised of bad bots, e-commerce was the second most targeted industry by bad bots in February. The sector witnessed an unexpected surge in bad bot traffic after the rise of the coronavirus pandemic.
Figure 5: Traffic distribution of the e-commerce industry
Let’s take a detailed look at how cybercriminals are targeting e-commerce firms through a real-world case study. We monitored the traffic of a top European e-commerce site that has hand sanitizers and face masks listed on its portal. As coronavirus fear increases, bots ramp up their search for face masks and sanitizers as shown in figures 6 and 7.
Figure 6: Search for hand sanitizers by bad bots.
Figure 7: Search for face masks by bad bots.
These automated attacks could be aimed at performing denial of inventory attacks, hoarding these essential products to sell in black markets, or even scraping product details to list similar products on malware-ridden sites to scam people.
As the coronavirus threat intensifies, bots will drive the infodemic much further, continuing to be an efficient tool for cybercriminals, nation-state actors, and conspiracy theorists alike. The impact of information - true or false - especially in times of fear, uncertainty and confusion is greater. Because communication channels are diverse, authorities have very little control of Bot activity. In the coming months, we expect the use of bots to accelerate due to the COVID-19 pandemic and the US presidential election.
Nikhil Taneja
Managing Director-India, SAARC & Middle East, Radware
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.





























