
With India going through a major digitization drive and with the current security landscape under constant threat, the rise in the demand for integrated endpoint security solutions has gone up. The endpoint security market finds huge opportunity to proliferate in the next five years. But are these solutions sufficient to avert advanced threats?

The threat landscape in the country, and the world, is changing by the minute. According to a report by Data Security Council of India (DSCI), India's cybersecurity market size is about $4 billion, which is expected to grow to $35 billion by 2025. According to Gartner, the overall IT spend on security in India in 2016 is expected to reach $1.12 billion, 10 percent up from $1.01 billion in 2015.
Putting forth his views on the same, Altaf Halde, Managing Director Kaspersky Lab South Asia says, “It is important to understand the gigantic growth we are expecting within the next 2 years, to understand the impact area of all potential threats -
* By 2018, we are expecting that one in five people in the world, that’s in excess of 1.5 billion people, will be shopping online.
* By 2017, 60% of e-commerce business will come through smart phones.
* More and more attacks are being discovered every month, that can go very long, undetected
 In light of all these facts, the threat landscape in India is not just very complicated, it offers unique challenges.
In light of all these facts, the threat landscape in India is not just very complicated, it offers unique challenges.
* There are significant cyber security threats to buyers, sellers and payment system providers alike. Not to mention businesses, especially the solely online ones, who have everything at stake
* Very intelligent, smart attacks such as ProjectSauron will target highly sensitive businesses
* During high activity seasons, such as sales during festivals, criminals try to connect their malicious campaigns such as phishing.”
According to Sunil Kripalani, Senior Vice President - Global Sales & Marketing – eScan, endpoint security has now extended beyond the fixed desktops to laptops and BYOD devices that are also used in other unsecured Wi-Fi environments. “This invariably puts the risk of being compromised by a cyber-attack or malware, which might use the host endpoint as bots to enter into a network later. Apart from this the usage of storage devices which are not authorized or compromised could also be carrier of the malware to bring down a network when used in a network which is not using endpoint security to protect its network.”
Data is the single most vital asset that corporations own today; a security breach results in financial losses and causes a bigger dent on reputation. Supporting his views with his own observations,
Murali Ramalingam, Country Manager-Sales, Ixia says that Indian enterprises have started to realize that cyberattacks affect their business continuity, agility, and brand image equally. “We have noticed that companies across verticals are now investing significantly in network security solutions to fend off future attacks. Growth in online and digital data has played a significant role in driving the security market in India. Indian enterprises are more vulnerable to security attacks as they have not adopted and implemented the best of security solutions available.” He further continues, “We recommend organizations to look at security as a continuous practice than just an IT function. Test before you deploy, monitor when you go live and secure continuously, do not wait for an attack to occur.”
 Ajay Dubey, Senior Channel Manager, Forcepoint opines that the enterprise and consumer threat landscape is in for a tectonic shift in the coming times. There would be the need of a blend of technology and strategy to combat security threats as cyber threats today are more complex and targeted and customized to attack a particular network’s vulnerabilities. “A most visible change in the landscape now is the fact that customers are investing in Forensics and are interested in the ‘Post Facto’. They are looking at solutions that leverage data – modelling, big data, analytics to identify anomalies in user behaviour to protect networks,” he says.
Ajay Dubey, Senior Channel Manager, Forcepoint opines that the enterprise and consumer threat landscape is in for a tectonic shift in the coming times. There would be the need of a blend of technology and strategy to combat security threats as cyber threats today are more complex and targeted and customized to attack a particular network’s vulnerabilities. “A most visible change in the landscape now is the fact that customers are investing in Forensics and are interested in the ‘Post Facto’. They are looking at solutions that leverage data – modelling, big data, analytics to identify anomalies in user behaviour to protect networks,” he says.
It is indeed becoming important for organisations to reshape their cybersecurity approach in order to survive the digital cyber attack. “IT Security needs to evolve from a support conversation to become a boardroom agenda. CTOs as well as CSOs should now play a bigger role for IT to demonstrate that technology can deliver what the business wants in a secure fashion,” he further says.
In the last few years, there have been numerous systematized security breaches in India that have caused data losses worth millions of dollars. The recent ATM security breach in the country should be an eye opener for the enterprises and government to take network security seriously. There is immense need for developing strong security practices within banks and have separate IT/IS and cyber security budget.
“The cyber security landscape and climate feels like there’s storm after storm happening almost on a daily basis, and reminds us that when it rains it pours. Data breaches are not stopping, and emerging cyber threats are leaving bigger business impact than ever. For many individuals and organizations, information technology (IT) is no longer an ancillary part of the business but a key ingredient for success,” observes Jitendra Ghughal, National Channel Manager, India & SAARC, Fortinet.
According to him, innovation is a good thing because it makes our lives better. But it can also represent another entry point for threat actors and hackers. “For example, LinkedIn made it easier for professionals to stay connected but also introduced additional risks. Clearly, there weren’t data breach reports about 100 million LinkedIn accounts being compromised 15 years ago because there was no LinkedIn at that time. Why does this matter? Each new innovation is yet another opportunity or entry point for the bad guys to launch an attack against a potential victim,” he says.
 The move to ramp up local cybersecurity expertise is well timed to augment the country’s focus on Digital India, a campaign mooted by Prime Minister Narendra Modi, to use technology in government and offer government-to-citizen services. The Indian government has been bullish in its digitization efforts. Digital India, the Aadhaar movement, and becoming a cashless economy are just a few examples. “It’s important to realize that as we digitize and rely more on technology, we become more vulnerable to cyber attacks. India is an attractive target for cyber attacks, thanks in part to geopolitical tensions and relatively weak defences due to an underinvestment in cyber security,” says Vishak Raman, Senior Regional Director for India and SAARC – FireEye.
The move to ramp up local cybersecurity expertise is well timed to augment the country’s focus on Digital India, a campaign mooted by Prime Minister Narendra Modi, to use technology in government and offer government-to-citizen services. The Indian government has been bullish in its digitization efforts. Digital India, the Aadhaar movement, and becoming a cashless economy are just a few examples. “It’s important to realize that as we digitize and rely more on technology, we become more vulnerable to cyber attacks. India is an attractive target for cyber attacks, thanks in part to geopolitical tensions and relatively weak defences due to an underinvestment in cyber security,” says Vishak Raman, Senior Regional Director for India and SAARC – FireEye.
He further points out that advanced attacks aren’t the only concern. Cyber criminals are also growing more sophisticated and more successful. “Over the past year, FireEye has observed a sharp rise a cyber threat called ransomware. FireEye found ransomware detections increased 292 times from November 2015 to February 2016,” says Vishak.
At the same time it is also true that today organizations are spending millions of dollars on traditional endpoint security and losing the battle against advanced threat groups. “This is because most existing endpoint security solutions use conventional antivirus and anti-spam software and host intrusion prevention services that are useful against commodity malware but ineffective against advanced attacks,” he adds.
Factors driving endpoint Security market...
Verticals that can be seen to actively adopt end point security solutions are e-commerce, finance, banking, telecom, healthcare, IT & Telecom, energy, online payment systems and many more. However, in keeping with the Indian government’s very aggressive stance on going digital, the government leads the race in adopting endpoint solutions.
 “The endpoint security market in India as well as the globe are primarily driven by factors such as – need to address IT risks, growing trend of Bring Your Own Device (BYOD) in organisations and increasing number of internal threats. Moreover, the growing demand for mobile and tablet security solutions is also driving the demand for endpoint security. The verticals that are increasingly adopting endpoint security solutions include BFSI, healthcare, and IT and Telecom verticals, Government and defense verticals,” asserts Nilesh Jain, Country Manager, (India and SAARC) - Trend Micro.
“The endpoint security market in India as well as the globe are primarily driven by factors such as – need to address IT risks, growing trend of Bring Your Own Device (BYOD) in organisations and increasing number of internal threats. Moreover, the growing demand for mobile and tablet security solutions is also driving the demand for endpoint security. The verticals that are increasingly adopting endpoint security solutions include BFSI, healthcare, and IT and Telecom verticals, Government and defense verticals,” asserts Nilesh Jain, Country Manager, (India and SAARC) - Trend Micro.
Ajay concedes that endpoint security is the first step to fight against cyber attack. “The endpoint security market is specifically driven by factors, such as the need to mitigate IT security risks and increase in the frequency of internal threats. In a tossup between the conventional method of having core investments in central location and pushing updates to end point versus a modern approach of equipping the end points with analytics and other tools, the modern approach is gaining traction,” he adds.
Increased penetration of mobile devices is further fuelling the market growth. People are nowadays increasingly using their mobiles to shop online, pay bills and access social networking sites. Jitendra states that while a majority of businesses are already leveraging the advantages of connected IoT devices, 92% of security professionals are concerned about the security challenges posed by these billions of devices. “Many of these devices are “headless” offering few or no security or management controls. This has exponentially increased the attack surface and left IT struggling to manage IoT devices using complex architectures consisting of numerous point solutions. So IoT is a security problem for all verticals − BFSI, Government, Healthcare, Retail, Education, Manufacturing or even home networks,” he says.
“The primary driving force behind the endpoint security market is the sheer numbers,” points out Altaf. “Billions of people are expected to come into the net of active online services. As more and more people get online to buy, sell, watch movies, shop and game, the need for endpoint security is growing rapidly by the minute.”
The incidents that are being reported internally within organisations and the inability to investigate these incidents using the existing tools is driving security managers to look further. “Organisations are spending significant amounts to engage consultants to help with their incident investigations; security teams are realising that they need to realign their investments to ensure effective protection against these threats. While we are seeing accelerated adoption within the Banking and Financial Services industries we are also seeing quick adoption by the IT/ITES companies as well for their internal security,” says Sudeep Das – Manager – Presales – RSA.
 Manoj Taskar, Country Manager - Tenable feels that factors like remote working, BYOD and cloud have changed the end-point environment in a significant way. The need for visibility of endpoint vulnerabilities coupled with compliance requirements at the infrastructure level, till the last point, are the driving factors. “The more we move to remote working, the more the importance for endpoint visibility and compliance to policies,” he says.
Manoj Taskar, Country Manager - Tenable feels that factors like remote working, BYOD and cloud have changed the end-point environment in a significant way. The need for visibility of endpoint vulnerabilities coupled with compliance requirements at the infrastructure level, till the last point, are the driving factors. “The more we move to remote working, the more the importance for endpoint visibility and compliance to policies,” he says.
Large organizations vs smaller organizations – Which is more vulnerable?
India has a thriving Micro, Small, Medium Enterprises (MSMEs) ecosystem of over 40 million business firms. They are also a ripe target for cyber attackers as they are more connected to the Internet than ever before, yet their cyber security capabilities are more limited than businesses elsewhere. Many Indian MSMEs lack the technology, intelligence and expertise required to deal with even relatively modest cyber security threats.
It must not be forgotten that attackers today target 'low-hanging fruit' in order to gain dominance over an organization. It can be through the company’s vendors, phishing of employees and staff to get unauthorized access to business sensitive data, etc. SMBs need to be as cautious as large businesses.
Most importantly, Mid-level organisations do not have the budgets that larger organizations do. This definitely exposes them to greater security threats, because hackers have understood this and have been attacking small-and-mid-sized organisations more and more in the past decade. The main threats that these organizations face are in the form of physical attacks on systems, authentication attacks, and malicious internet content. As per a report released by PwC, small firms are cutting down their investment on security, which is a huge mistake.
 “SMEs are preferred targets for cybercriminals as automation makes it easy to attack them by the thousands, and far too many of them are easy targets. It is the data that makes a business tempting, not the size – especially if it is relevant data, such as customer contact info, credit card data, health data, or valuable intellectual property,” points out Nilesh.
“SMEs are preferred targets for cybercriminals as automation makes it easy to attack them by the thousands, and far too many of them are easy targets. It is the data that makes a business tempting, not the size – especially if it is relevant data, such as customer contact info, credit card data, health data, or valuable intellectual property,” points out Nilesh.
“SMB and mid-level organization are often seen to be struggling, more so because of the mindset of being a small organization and not a matter of interest for cybercriminals. In the absence of appropriate security controls, organizations mostly tend to delay in incident detection and response and may sometimes even fail to detect incidents. However, some of the SMBs are relying on cost effective cloud security solution or moving their business applications in cloud to address application availability and security concerns along with the cost,” observes Shibu Paul, Regional Director (IN, GCC & SEA) - Array Networks.
It is important to note here that smaller organizations increasingly serve as vendors, contractors, and business partners of bigger firms, and as such they may have trusted access to the networks and data of these partners. SMEs indeed need to improve their security within their budget by going for cloud based solutions.
Large organisations on the other hand are relatively better prepared to battle the online threats. They have sufficient budgets and manpower allocated to manage their digital security. This makes it much easier to understand the security threats for the organization and hence, look for the best integrated security suites.
However, despite an experienced CISO leading a competent team, there have been some common challenges that even the larger organisations face -
* Under-estimating potential threats: Even if they do not seem very threatening currently, some threats can quickly spiral out of control.
* Distribution of the budget: Often, more budgets are routed to some areas, while other areas suffer from being short-funded. This leaves some very crucial endpoints open to large threats.
 * Understanding which suite works best for the company: Very often, companies go for the most popular integrate security suite that is prevalent in their industry. Sometimes, that may not be the best suite for that particular company. Each organization, due to its unique structure, needs a customized security solution. What works for most companies, may not work for you. So, there’s a need to understand what are the best suite options for a company.
* Understanding which suite works best for the company: Very often, companies go for the most popular integrate security suite that is prevalent in their industry. Sometimes, that may not be the best suite for that particular company. Each organization, due to its unique structure, needs a customized security solution. What works for most companies, may not work for you. So, there’s a need to understand what are the best suite options for a company.
* Keeping the security budget constant through the years: As security threats increase, the solutions need to fast adapt. Newer, better technology sometimes costs more than older one. This means that the security budgets need to grow, with the times. A budget that worked last year, may not work this year. And in the compulsion to maintain it, companies sometimes keep a large part of the business either unsecured or under-covered.
There is however no difference between the security required by an enterprise and that required by a small business other than in the scale and resources to manage it. “Small businesses face a significant competitive disadvantage if they cannot respond effectively to incidents, and face the same penalties as the enterprise. The vanishing perimeter due to cloud-based services, social media, remote offices, Internet of Things, roaming workers and BYOD brings new security challenges,” opines Sunil Sharma, VP- Sales (India & SAARC), Sophos.
“The truth is that everyone with a computer on the Internet is vulnerable, and disruptive attacks have become a legitimate issue. Businesses must plan and prepare accordingly. The best way is to detect threats before it disrupts the system of the victim,” suggests Vishak.
“India is still in a stage where the ability to understand what’s going on in the network is still in an early stage when compared to other countries. This is something that has to be addressed because today’s networks have no boundaries. Cyber attacks can happen in India as it can happen in Australia or in any other part of the world. We have to make our customers understand it’s no longer a question of if I will be breached − it’s a question of when I will be breached,” Jitendra clarifies his point.
Regardless of size of the company, security would depend upon scale of network and tools implemented. It is often observed that nature of business would determine the amount of risk a business is exposed to. For instance, an SMB bank would be more vulnerable to cyber-attack than a SMB IT services company. Budget for security or for any investment comes from company’s topline. Having a huge security budget and spending a lot on security doesn’t still guarantee being safe. The recipe here is to employ right tools. There have been instances of biggest corporations from fortune 500 companies employing huge amount of security budgets but still got breached.
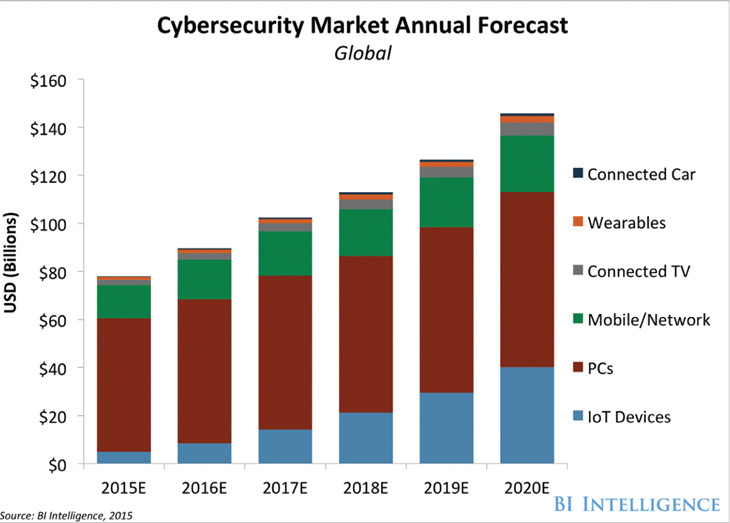
Sudeep however observes a steady rise in the level of awareness and purpose in large organisations to work on integrated security suites – the need to share information across tools to provide richer context to every incident investigations is a basic requirement for effective and complete response procedures. “RSA’s view is that realignment and reprioritisation of existing investments should allow any organisation to build capabilities around modern threats. The new generation security tools are not necessarily more capital intensive than existing security products; what is needed for organisations is to assess the efficacy of existing investments and plan the most appropriate plan to upgrade the approach towards security,” he says.
Is endpoint security sufficient to thwart threats?
So now the question is, with so many threats emerging every day, is having merely an endpoint security enough to avert them. The answer is no. While these are great for preventing a lot of attacks, many advanced threats will slip through.
Apart from endpoint security, businesses must try to also cover:
* Virtualisation Security
* Mobile Security
* Anti-Targeted Attacks
* DDoS Protection
* Security Intelligence Services
* Security for Data Centers
* Fraud Prevention
* Industrial Cyber Security
* Targeted Security for Business
Jitendra puts across several pointers on how a business can be far from getting breached or compromised. “The response to increasingly complicated networked environments needs to be simplicity. Securing these evolving environments requires three things:
 * Collaborative intelligence – Local and global threat intelligence needs to be shared between security devices, and a coordinated response between devices needs to be orchestrated centrally.
* Collaborative intelligence – Local and global threat intelligence needs to be shared between security devices, and a coordinated response between devices needs to be orchestrated centrally.
* Segmentation - Networks need to be intelligently segmented into functional security zones.
* Universal policy - A centralized security policy engine that determines trust levels between network segments, collects real time threat information, establishes a unified security policy, and distributes appropriate orchestrated policy enforcement
Sunil too vouches for an integrated approach to IT Security deployment that he feels is essential to stay safe from advance cyber threats. Few of the important steps to be followed is to implement a robust advance level security solution across gateway and endpoints, train & educate the employees on security policies and on the use of Handheld or laptop devices with utmost care while using in unsecured wi-fi networks and thirdly to create a strong IT security policy across organization.
And so...
Low awareness of the risks posed by cyber attacks is a big challenge to an organization in India, irrespective of its size, because today, it is far too easy to disrupt the operations of an Indian company with easily available tools. A sound security strategy that recognizes shifts in the threat landscape is thus the need of the hour that can help mitigate these risks.
Samrita Baruah
samrita@varindia.com
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.






























