
By Dr. Deepak Kumar Sahu, Editor-in-chief-VARINDIA
Identity and Access Management (IAM) is a critical framework for securing enterprises. It uses technologies, policies, and processes to ensure that the right people have the right access to the right resources at the right time. The two core functions of IAM are authentication (verifying a user's identity) and authorization (determining what a user can access).
According to experts, authentication is the first line of defense. While traditional methods like passwords, figure print Biometrics are prone to compromise, and normal figure print biometrics alone face new threats in an AI-driven world, a more robust approach is needed.
The increasing reliance on static biometrics, such as fingerprints, facial scans, and iris patterns, has indeed exposed vulnerabilities, as these identifiers are immutable—unlike passwords, they can't be changed if compromised. This has led to heightened risks of identity theft, fraud, and privacy erosion in data breaches
Key IAM components include:
● Authentication – Verifying users (Passwords, Biometrics, MFA).
● Authorization – Assigning rights/permissions to resources.
● Single Sign-On (SSO) – Enabling one login for multiple systems.
● Privileged Access Management (PAM) – Securing high-level admin accounts.
● Identity Governance and Administration (IGA) – Ensuring compliance with policies and regulations.
● Zero Trust Framework – “Never trust, always verify” approach to continuous access validation.
Security for enterprises is moving beyond static passwords and basic biometrics. The new focus is on behavioral biometrics, which analyzes unique user patterns like typing rhythm and mouse movements to detect anomalies. This "Biological Behavior Detection" serves as a powerful first line of defense. When combined with Multi-Factor Authentication (MFA), this layered approach creates a much stronger security posture, using both who a person is (biometrics) and how they act (behavioral biometrics) for effective protection.
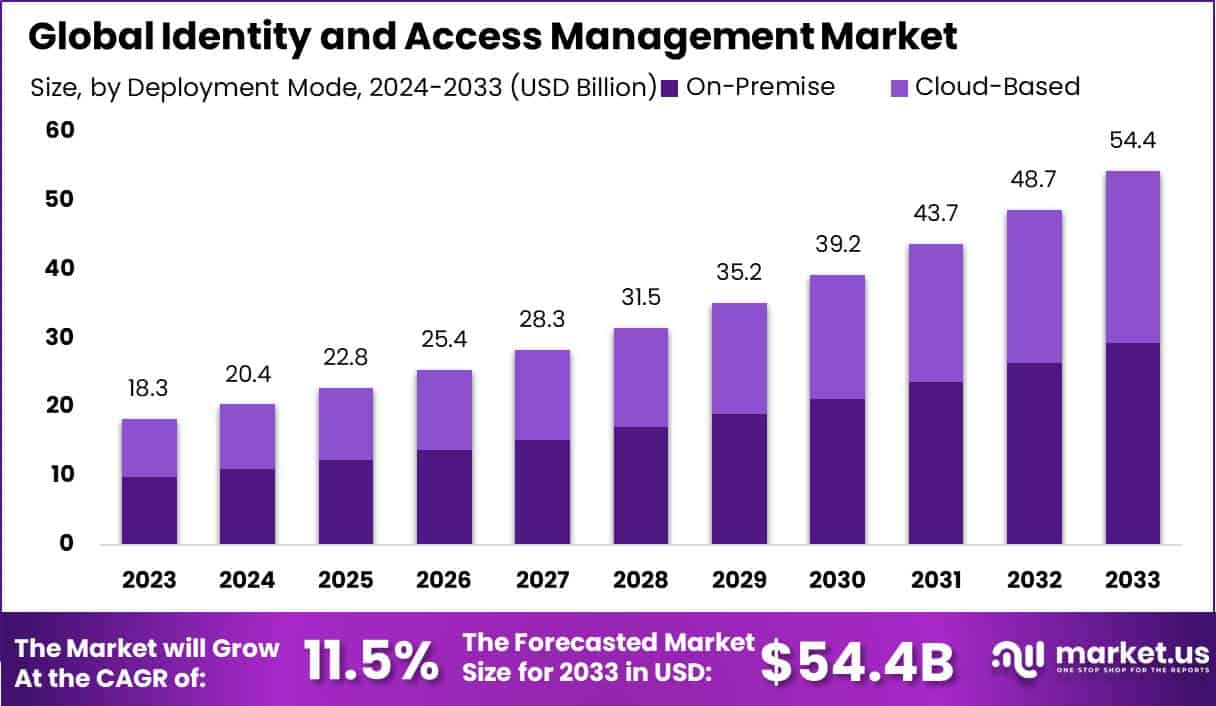
IAM is helpful in managing digital identities and controlling how those identities interact with corporate IT systems, data, and applications. As per the survey of VARINDIA ( Channel Leadership Survey), it estimates the market at USD 22.9 billion in 2024, growing to USD 34.3 billion by 2029, at a CAGR of approximately 8.4%.
|
Region |
Estimated Market Size Now |
Forecast Size (5–10 yrs) |
CAGR Range |
|
Global |
~USD 16–23 billion |
~USD 35–62 billion |
8%–15% |
|
India |
~USD 185 million–750 million |
~USD 600 million–1.5 billion |
8%–18% |
The global IAM market is surging amid rising cybersecurity threats, cloud adoption, regulatory requirements, and digital transformation. In India, heightened cyberattacks, regulatory mandates (like DPDP and RBI guidelines), and growth from sectors like BFSI and government are fueling demand.
OEM Presence and IAM Solutions
Several global OEMs (Original Equipment Manufacturers) dominate the IAM market, alongside niche providers:
● Microsoft (Azure Active Directory / Entra) – cloud-native IAM, SSO, MFA, conditional access, identity governance.
● Okta – cloud-first IAM with strong integrations for enterprises and developers.
● IBM Security Verify – advanced IAM with AI-driven risk analytics.
● Oracle Identity Management – enterprise-grade IAM with governance and compliance focus.
● Ping Identity – specializes in secure SSO, MFA, and Zero Trust architecture.( Acquired by Thoma Bravo)
● CyberArk – leading in Privileged Access Management (PAM).( Acquired by Palo Alto Networks)
● SailPoint – strong in Identity Governance and Administration (IGA). (Acquired by Thoma Bravo)
● ForgeRock – digital identity platform with large-scale deployments. (Acquired by Thoma Bravo)
Indian players like Zoho (ManageEngine IAM) and start-ups focusing on Aadhaar-linked or DPDP-compliant IAM solutions are also gaining ground. Secondly, InstaSafe provides cloud-based IAM solutions that support a Zero Trust security model.
How IAM Fights Growing Cybercrime in India
India is witnessing a surge in cybercrime—from financial fraud, phishing, ransomware, and identity theft to deepfake-enabled scams. IAM solutions are crucial in mitigating these risks:
1. Stops Unauthorized Access – MFA and adaptive authentication prevent account takeovers.
2. Protects Sensitive Data – Role-based access ensures only authorized employees can access critical information.
3. Prevents Insider Threats – Privileged Access Management (PAM) monitors and restricts admin-level misuse.
4. Supports Regulatory Compliance – IAM helps enterprises comply with RBI KYC norms, DPDP Act, and global standards like GDPR/HIPAA.
5. Enables Zero Trust Security – IAM enforces continuous monitoring, limiting lateral movement in case of breaches.
6. Fights Fraud – Behavioral biometrics, identity governance, and real-time monitoring reduce fraud attempts in BFSI and telecom sectors.
The inclusion of Biological Behaviour Algorithm builds on the principles by incorporating multimodal analysis for enhanced defense against unauthorized access. The algorithm leverages an Adaptive Cognito Engine (ACE) to process behavioral data alongside visual cues, aiming to replace traditional passwords in scenarios like online payments. Key features include:
Facial Emotion Recognition: Detects stress or fraud via micro-expressions.
Eye Tracking: Monitors gaze and pupil changes to verify intent.
Posture Analysis: Uses body movements to spot deviations from normal behavior.
Additionally, the algorithm cross-verifies behavioral datasets with official identifiers, such as social security numbers or their international equivalents, when available, to execute a final authentication step. This fusion of passive biometrics and verified identity data aims to establish a highly secure environment, ideal for critical applications like financial transactions.
IAM providers must integrate Biological Behaviour Algorithms(BBA) that analyze micro-expressions, gaze, posture, voice tone, and keystroke dynamics for continuous, context-aware authentication. Using adaptive engines to fuse multimodal signals enables dynamic trust scoring, strengthening defense against AI-powered fraud while keeping user experience seamless.
Compliance with frameworks such as GDPR, HIPAA, and DPDP must be built in with full auditability. Sector-specific uses span BFSI (fraud-proof KYC, secure payments), defense, healthcare, and enterprises—making behavioral biometrics the new frontier of digital trust.
See What’s Next in Tech With the Fast Forward Newsletter
Tweets From @varindiamag
Nothing to see here - yet
When they Tweet, their Tweets will show up here.





























